搜索结果: 1-15 共查到“hardware”相关记录224条 . 查询时间(0.101 秒)
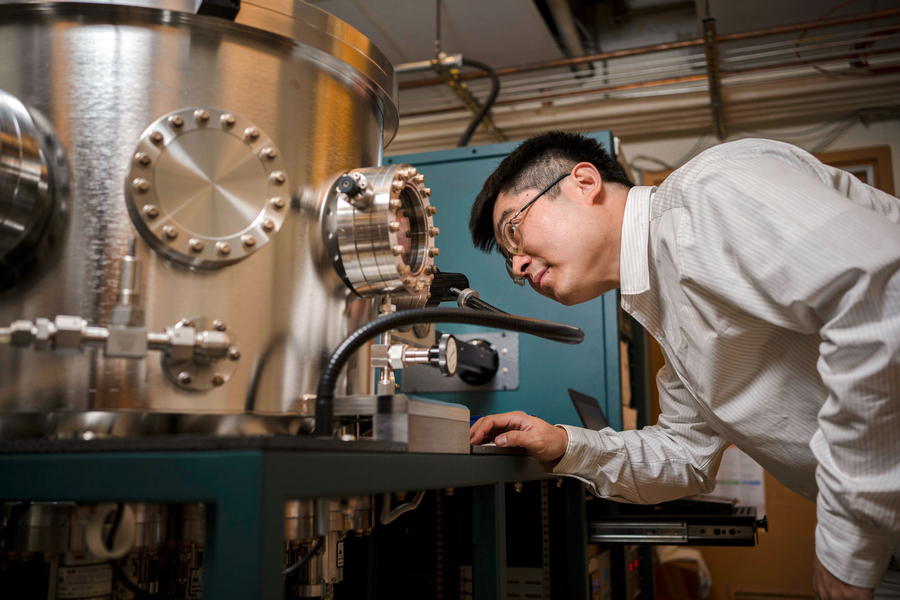

New hardware offers faster computation for artificial intelligence, with much less energy(图)
新硬件 人工智能 计算速度 模拟深度学习
2023/6/6


Researchers discover a new hardware vulnerability in the Apple M1 chip(图)
苹果M1芯片 硬件漏洞 数据安全 计算机安全
2023/6/20

Workshop tackles a critical gap slowing the development of new hardware technologies(图)
新硬件技术 车间 半导体技术
2023/6/9

New program bolsters innovation in next-generation artificial intelligence hardware(图)
人工智能 硬件 量子时代
2023/6/20
Researchers develop speedier network analysis for a range of computer hardware(图)
Researchers develop speedier network analysis range computer hardware
2021/3/12
Graphs -- data structures that show relationships among objects -- are highly versatile. It's easy to imagine a graph depicting a social media network's web of connections.But graphs are also used in ...
Hardware-Software Co-Design Based Obfuscation of Hardware Accelerators
hardware security logic obfuscation hardware accelerator
2019/9/19
Existing logic obfuscation approaches aim to protect hardware design IPs from SAT attack by increasing query count and output corruptibility of a locked netlist. In this paper, we demonstrate the inef...
SPAE a mode of operation for AES on low-cost hardware
secret-key cryptography AES block ciphers
2019/9/16
We propose SPAE, a single pass, patent free, authenticated encryption with associated data (AEAD) for AES. The algorithm has been developped to address the needs of a growing trend in IoT systems: sto...
Graph Similarity and Its Applications to Hardware Security
Graph Similarity Hardware Reverse Engineering Hardware Trojan
2019/8/30
Hardware reverse engineering is a powerful and universal tool for both security engineers and adversaries. From a defensive perspective, it allows for detection of intellectual property infringements ...
CPA on Hardware Implementation of COLM Authenticated Cipher and Protect it with DOM Masking Scheme
Authenticated Cipher COLM CPA
2019/8/22
Authenticated encryption schemes provide both confidentiality and integrity services, simultaneously. Correlation power analysis (CPA) can be a thread for authenticated ciphers, like all physical impl...
Blockchain-enabled Cryptographically-secure Hardware Obfuscation
IP Piracy Logic Locking Hardware Obfuscation
2019/8/19
Electronic chips in consumer, industrial, and military applications are targeted by untrusted entities in the design and fabrication process, aiming at reverse-engineering and Intellectual Property (I...
Hardware Implementations of NIST Lightweight Cryptographic Candidates: A First Look
Lightweight cryptography FPGA Authenticated cipher
2019/7/17
Security in the Internet of Things (IoT) is challenging. The need for lightweight yet robust cryptographic solutions suitable for the IoT calls for improved design and implementation of constructs suc...
SIKE'd Up: Fast and Secure Hardware Architectures for Supersingular Isogeny Key Encapsulation
SIKE post-quantum cryptography isogeny-based cryptography FPGA
2019/6/19
In this work, we present a fast parallel architecture to perform supersingular isogeny key encapsulation (SIKE). We propose and implement a fast isogeny accelerator architecture that uses fast and par...
On-Device Power Analysis Across Hardware Security Domains
side-channel power analysis cross-domain
2019/6/12
Side-channel power analysis is a powerful method of breaking secure cryptographic algorithms, but typically power analysis is considered to require specialized measurement equipment on or near the dev...


